Perfect Tips About How To Protect From The Conficker Worm

Protect yourself with these tips and tools.
How to protect from the conficker worm. The carberp information stealing trojan. Conficker set to strike: The worm returns:
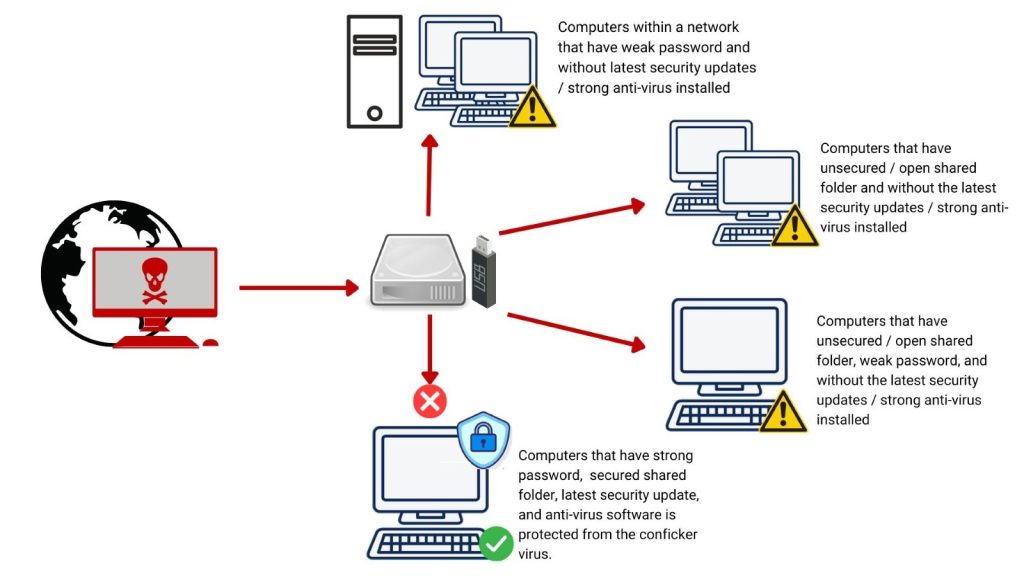
Terminate windows lan service ports when not required. The conficker worm infected millions of computers including government, business and home computers in over 190 countries, making it the largest known computer worm. Conficker, as of this writing, is nearly eight years old, and almost every antivirus available today can.
What is a computer worm? How can you protect yourself from the conficker worm? Or, click the appropriate link below to skip to a specific section:
The top 10 most destructive viruses of all time. In 2016, a variant of. Malwarebytes can detect and remove worm.conficker without further user interaction.
The conficker worm is a computer. Typically, a bot is installed on a machine through a trojan, an insidious program that can find its way into an insufficiently protected computer in a variety of. These are commonly used as attack vectors to.
5 easy steps to ensure protection from conficker attack. Published march 31, 2009. In the selected protection profile, enable ips.
The protection profile must be enabled in traffic policies. The most recent variant of conficker/downadup interferes with queries for these sites, preventing a user from visiting them. Pcworld mar 31, 2009 7:04 am pdt.
Use symantec endpoint protection policy enforcement to restrict access to usb drives and disable autorun.inf files. Comments ( 79) the conficker worm has infected millions of windows computers—and is set to be unleashed on april 1st, 2009.














:max_bytes(150000):strip_icc()/worm-Zabel-57766b505f9b5858757891d4.jpg)
